Enriching Sentinel with data from Virus Total
Introducing Total Virus
The Virus Total website is a well-known service by the cybersecurity team for allowing you to track various IoCs (Indicators of Compromissed) such as file hash, IP, domain or URL based on a simple search.
Virus Total has a subscription modality where it is free and has limits for consultations, in order to avoid its use by bots or third-party systems.See the details below and note that we have our API Key here even though it is a free account:

Solution on Sentinel
Since we have the possibility to integrate Virus Total data with Sentinel alerts and incidents, the first action is to install the Solution:

When installing the solution, you will see the information screen on the left that includes 9 playbooks that will collect incident, alert, domain or file data to search and correlate Sentinel data with Virus Total.The next step is to click on
Automation –> Playbook templates and install the playbooks, for this you can filter by the word “total virus” and use the
Create Template button to open the playbook installation window in your environment:

On this screen you will see that it is not yet necessary to connect your API Key or Log Analytics, this will be done after the
deploy when it opens the Logic Apps design screen:

Note that when opening the Logic Apps tasks and sequence you will see that the Virus Total and LogAnalytics connection will have the warning symbol and the save button will not work until you fix the connections.For this, the first time you will need to click on
API Connections and inform the data of both Virus Total and Log Analaytics that will be used. Below is the example of connection with Virus Total:

In the next connectors you will no longer need to configure the connections, as it will allow you to use the connection already configured in previous playbooks, like the image below:

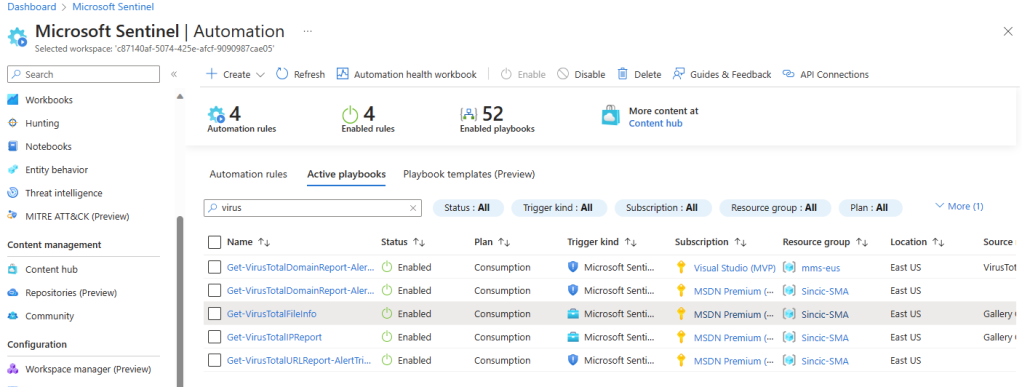
Remember that you will need to connect both the Virus Total and Log Analytics API (workspace ID and Key).Once configured, now after opening all the tasks and indicating the connections you will be able to save the Logic Apps and you will see that it will appear in the
Active playbooks tab :
Creating the Automation
Now that we’ve imported the solution and created the playbooks we want to use, the next step is to create the rule to run it, called an
Automation Rule .To do so, click on the
Create button –
-> Automation Rule and indicate the name of the rule and the trigger (trigger), which can be a new incident, a changed incident or a new alert.
When choosing the type of trigger, use the Run Playbook action to choose one of the triggers we created in the previous step:


When creating the rule there are several forms of filters that you can use, for example to detect that there is a file that will be analyzed since one of the playbooks is specific for hashing. You can also filter only for certain types of incidents or alerts.
Conclusion
Integrating different services to have IoCs from different sources will help a lot in your incident analysis.Also being tested right now in private preview widgets to bring data from Anomali, Record Future and Virus Total when you are investigating an entity (Entity) but that is another post in the future 🙌
Trackbacks & Pingbacks