Using Application Insights Log Analytics to detect anomalies in Web Apps
In a previous post I discussed the use of the Application Insights Log to view attacks and anomalies https://msincic.wordpress.com/2021/09/08/using-azure-application-insigths-in-vulnerability-analysis/
However, I saw the need to complement for some who asked me to integrate queries with MCAS logs, Defender and others.
Assuming that in all tools we will use KQL (Kusto Query Language) the first step is to write the command for this and bring the log like the image below:

In the query above, it is possible to bring the data that are in the dashboard of the previous article, but because it is written in KQL, you can customize the columns, formats and filters what interests you best.
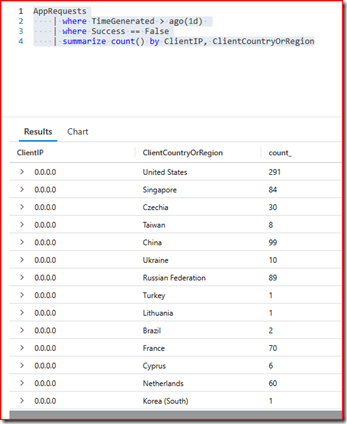
For example, you can alter the original query to bring the IPs by countries that consulted the pages of your site the most to detect origins that you want to filter and block on the firewall:
AppRequests
| where TimeGenerated > ago(1d)
| where Success == False
| summarize count() by ClientIP, ClientCountryOrRegion
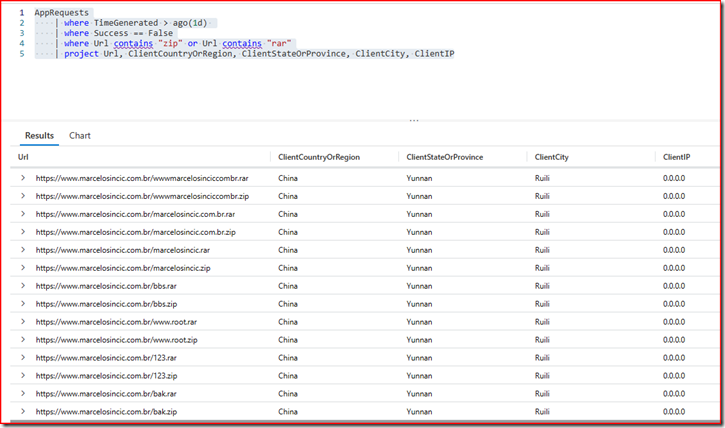
Another example is to filter requests that tried to download zipped files directly from your website, like the example below:
AppRequests
| where TimeGenerated > ago(1d)
| where Success == False
| where Url contains “zip” or Url contains “rar”
| project ClientCountryOrRegion, ClientStateOrProvince, ClientCity, ClientIP, Url
A third example is that I can identify SQL Injection attempts from the basic commands used for this type of vulnerability exploitation:
AppRequests
| where TimeGenerated > ago(1d)
| where Success == False
| where Url contains “select” or Url contains “union”
| project Url, ClientCountryOrRegion, ClientStateOrProvince, ClientCity, ClientIP

Conclusion
With the use of your application’s stored logs, it will be possible to visualize the main attacks and how to defend yourself by improving your application and having activity monitoring.
Cheers! I’m so happy I stumbled across this blog post – it’s been a real eye opener and also provided me with a load of new knowledge. Thanks for sharing your wisdom!
The text discusses the integration of queries with MCAS logs, Defender, and other tools using KQL (Kusto Query Language). It provides examples of customized queries to retrieve specific data from the logs, such as filtering by client IP and country, filtering requests for downloading zip or rar files, and identifying SQL injection attempts. The conclusion highlights the importance of using application logs to visualize attacks and improve application security.
Wayne